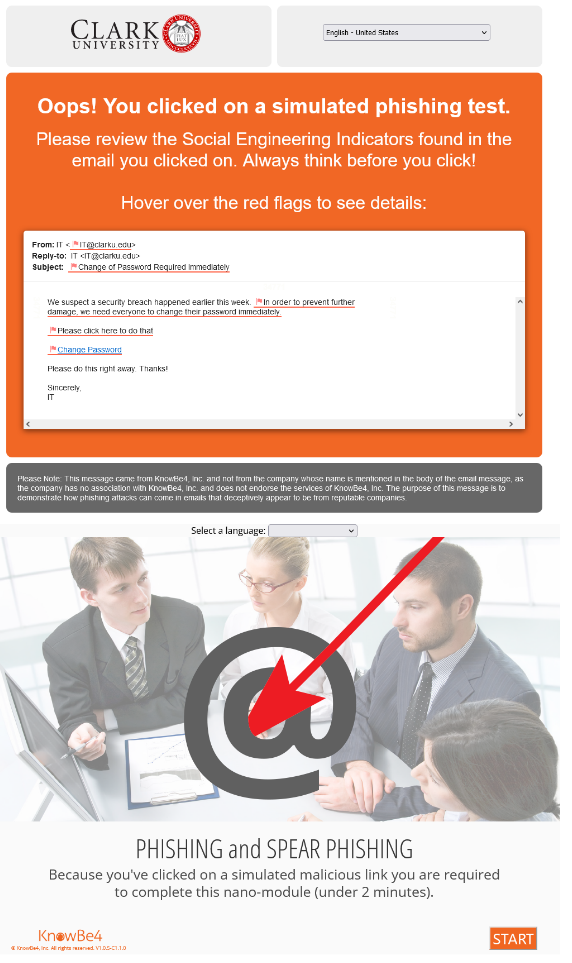
You have your passport, you have your bags packed, and you’re excited to get going. But wait! If you plan on connecting to your Clark account when travelling, preparing your MFA in advance can make your trip much easier.
When travelling or otherwise, ITS recommends using the Microsoft Authenticator app as your primary MFA factor. This app can be installed on multiple devices, and will allow you to authenticate into your Clark account from anywhere your devices can connect to the internet – regardless of cell service or phone number.
1. Adding Authenticator as a Factor
Before boarding the plane or hitting the road, be sure that Microsoft Authenticator is your primary MFA factor. Authenticator can approve your login via internet rather than using a text code that requires a specific phone number. In fact, usually Microsoft will default to using Authenticator if it is included as your factor since it is the most secure.
Click here https://mysignins.microsoft.com/security-info and log in if prompted.
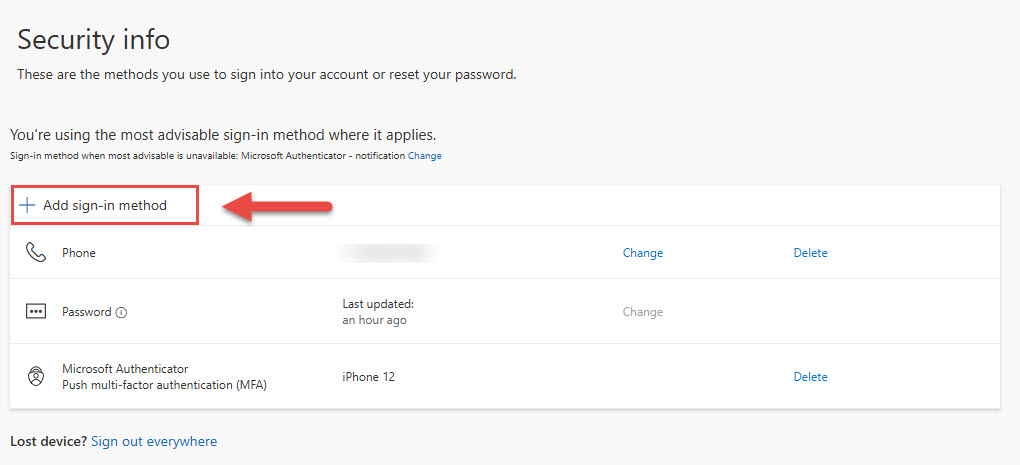
If Microsoft Authenticator is not included in your list of factors.
-
- Click Add sign-in method
- Choose Authenticator App
- Click Add, and follow the prompts
- If you need additional information, click here to see instructions on setting up MFA.
- When complete, check that Authenticator is listed as your default sign-in method again.
- If not, follow the instructions below.
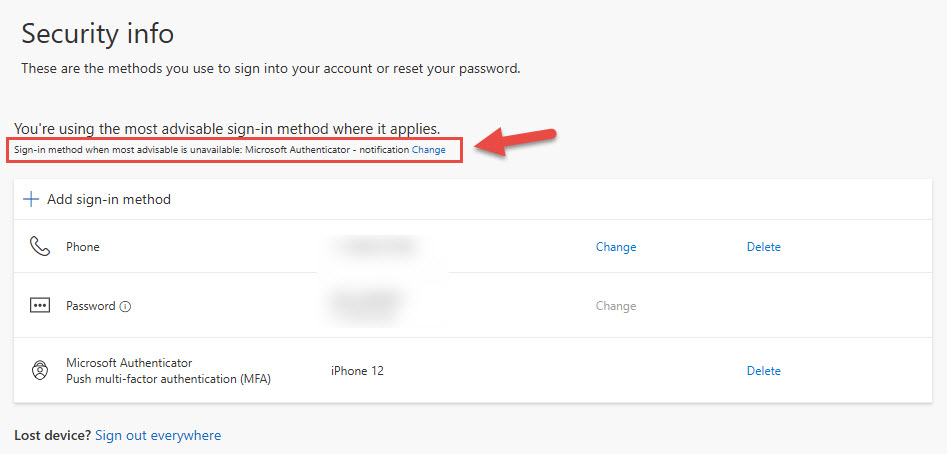
Once complete ensure that your Sign-in method when most advisable is unavailable is Microsoft Authenticator – notification. If not, click Change and choose “App-Based Authentication – notification”.
2. Installing Authenticator on Another Device
Now that Authenticator is your primary factor, you can install the app on multiple internet-connected devices to give you lots of flexibility when travelling. However, be sure to only install it on devices that you are the sole user of to prevent security issues.
Before beginning this process, be sure that the device with Authenticator set up as your primary factor in step 1 is connected to the internet.
- Download Microsoft Authenticator to your new device. Be sure that it’s published by Microsoft.·
- Launch the application
- Choose Work or School account
- Enter your Clark email address
- When prompted log in with your usual Clark credentials
- At this point, Microsoft will attempt to authenticate your login using your primary factor – the Authenticator app on your first device. Follow the prompts on your first device to authenticate your new device
From now, when authentication needs to happen, the Authenticator app on both devices (as long as connected to the internet) will prompt you to approve your login.
If you have any questions about this process, please contact the Help Desk at helpdesk@clarku.edu, 508-793-7745. Remember that we can support you more easily if you contact us before travelling.




 Our monthly information security articles are written by
Our monthly information security articles are written by