Email is a critical communication tool, and as a result, it’s important for all of us to be vigilant and able to spot phishing emails that attempt to compromise our personal and community information.
What is Phishing?
Phishing is the process in which malicious people try to trick you into giving out sensitive information or taking a potentially dangerous action, like clicking on a link or downloading an infected attachment. They do this using emails disguised as contacts or organizations you trust so that you react without thinking first. It’s a form of criminally fraudulent social engineering.
Phishing is one of the most common ways that attackers try to access our data and commit fraud. Phishers pose, usually via email, as a someone you know and lure you into revealing sensitive personal information, downloading malicious software or sending money or gift-cards.
How can I spot Phishing?
While Clark’s advanced security will do much to prevent many phishing emails reaching your inbox, it’s up to each of us to remain vigilant. Phishing emails can look like any other email. Some claim to offer free drinks from your favorite coffee shop, while others may pretend to be from a familiar department on campus.
Phishing emails often have the following characteristics:
- They will often appear to come from a Clark email address, but instead will be ‘spoofed’. Spoofed email addresses look similar but are actually different – similar to presidentsoffice.clarku.edu@gmail.com.
- For Staff and Faculty: Look for the [EXT] label in the subject which indicates an email was sent from outside Clark. If you see an email that looks like it came from a member of the Clark community, but has the [EXT] label, be cautious.
- Make requests for personal information (usernames, passwords, account numbers)
- Alarming and urgent statements instructing you to act immediately
- Slight alterations of well-known organization names (e.g. IT department, instead of ITS)
- Awkward writing style, misspelled words, or poor grammar are common, but phishers are becoming more sophisticated and polished in their writing.
What do I do if I suspect a message is a Phishing scam?
If you receive an email from someone that just feels out of place then you should report it. It is always better to ask ITS to investigate the email (by using the Phishing Alert button – see below), than open a malicious one that can spread malware and infect your device and even steal your information.
In a change to our previous advice, we ask that you no longer forward suspected phishing emails to anyone, including the Help Desk. Instead, please follow the instructions below to report the email in the most secure way.
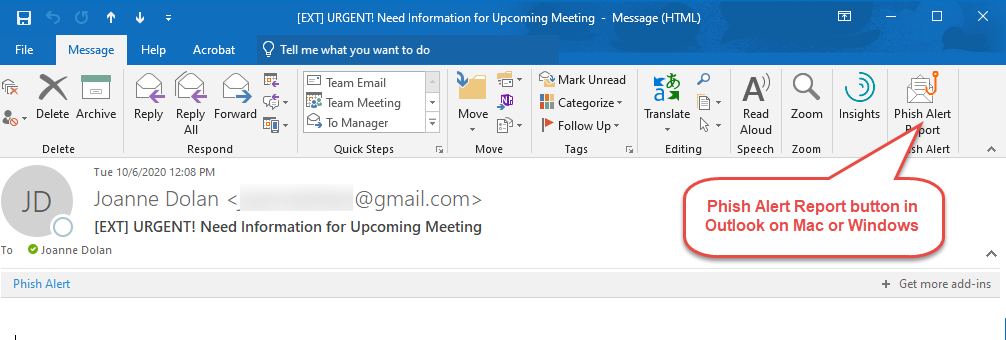
Outlook on Windows or Mac
- Click on the Phish Alert Report button in the top right of the email window.
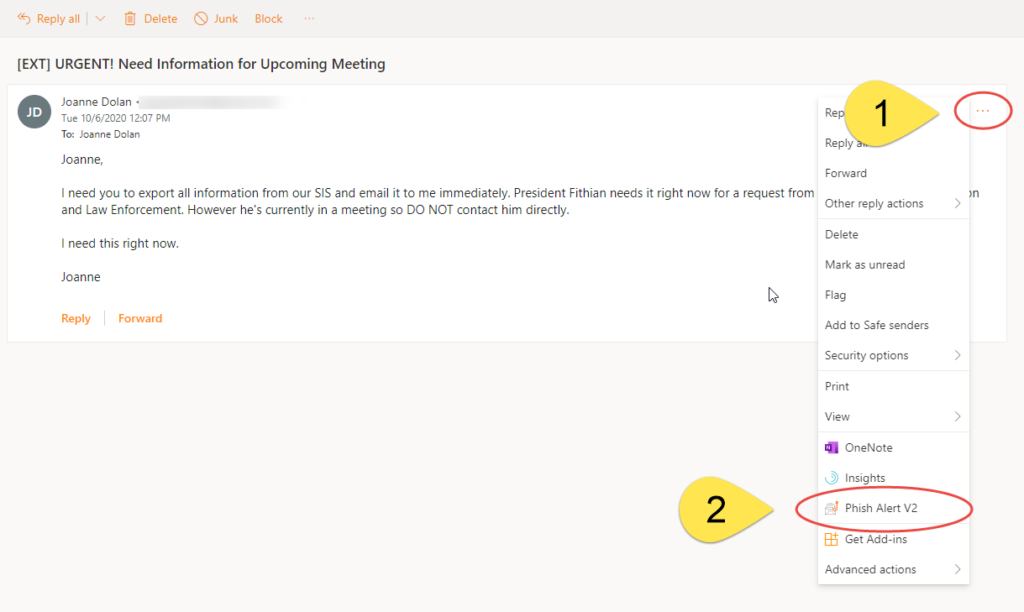
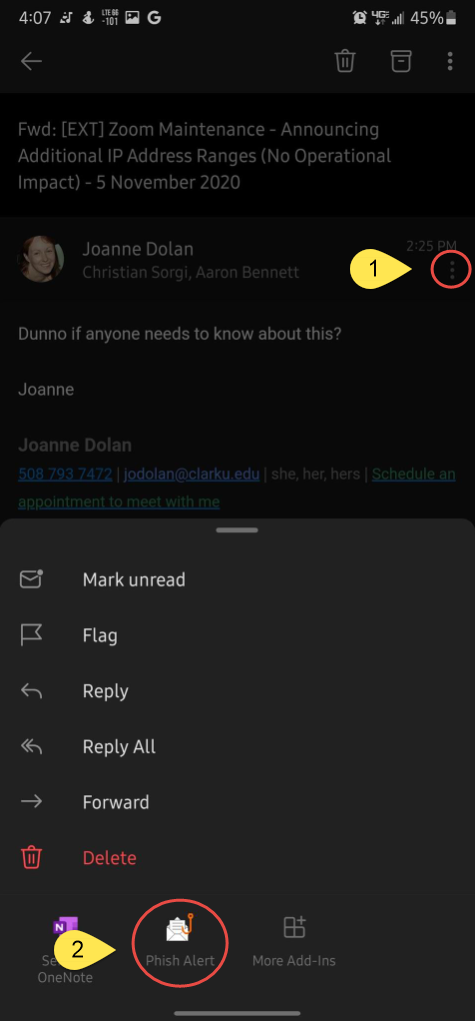
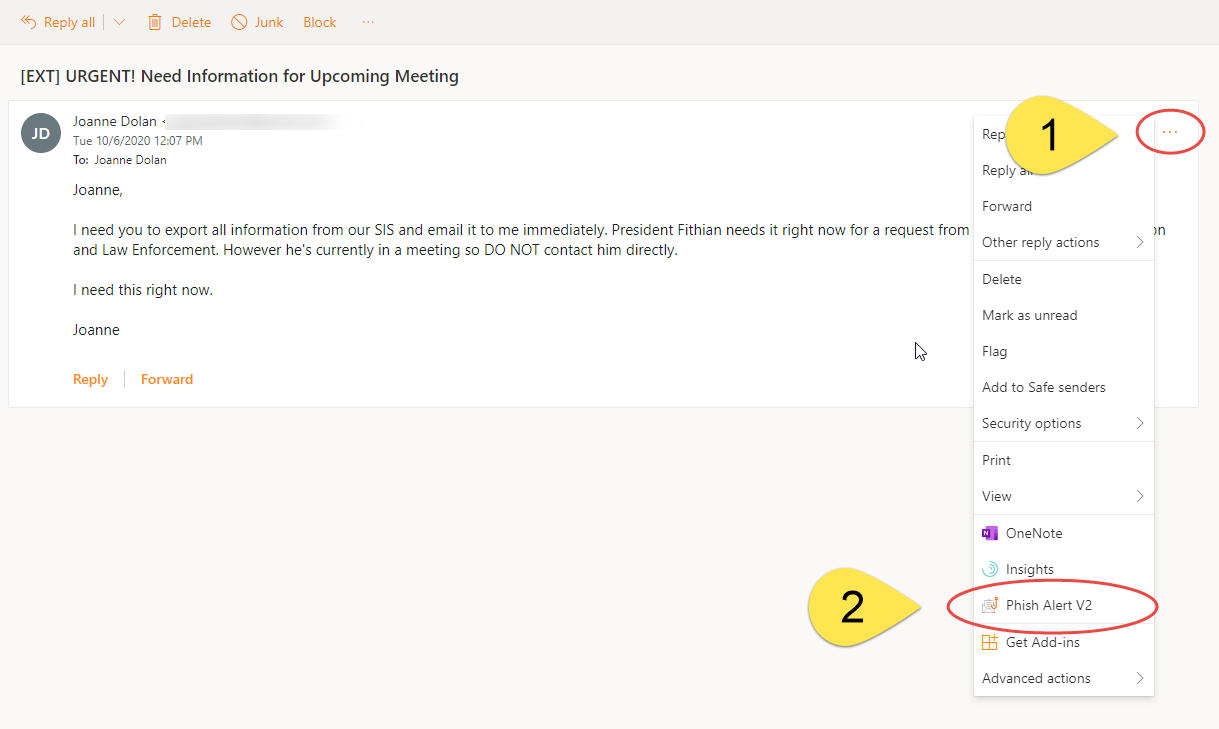
Outlook Online
- Click on the More Actions (three dots) button in the top right
- Click on the Phish Alert V2 option
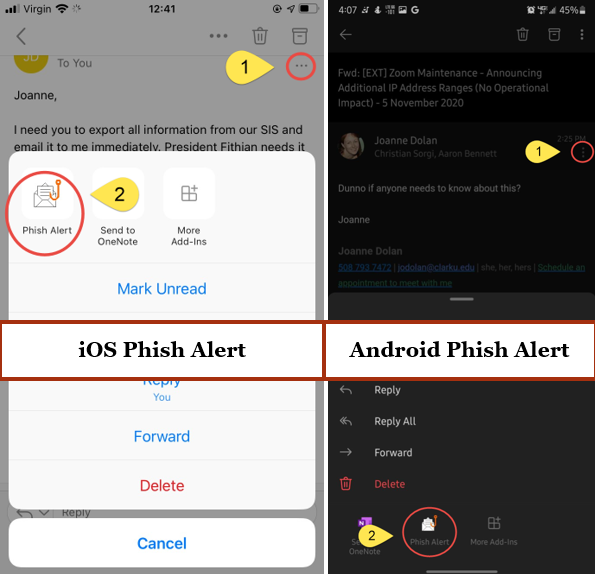
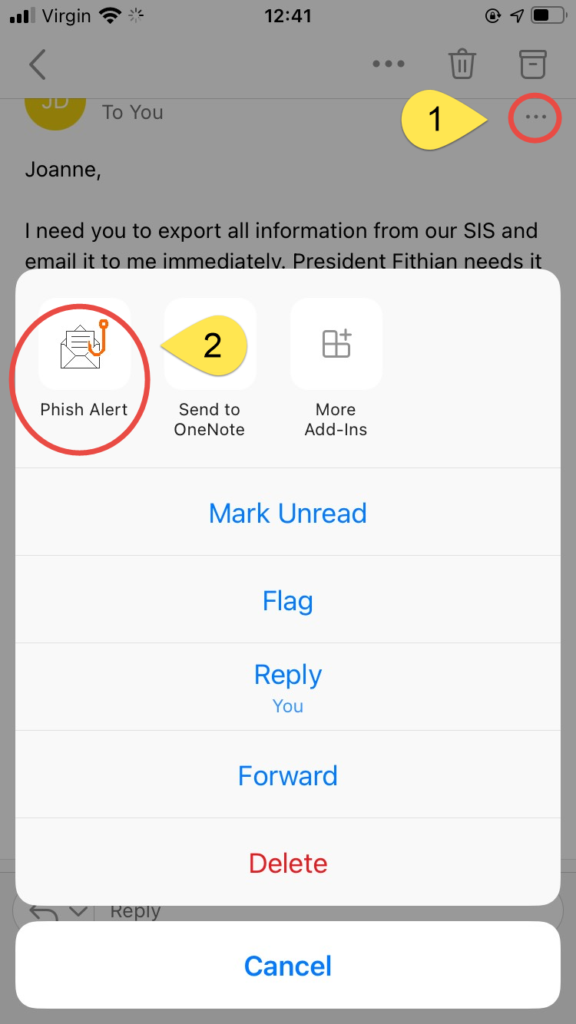
Outlook App on iOS or Android
- Click on the More Actions (three dots) button in the email
- Click on the Phish Alert button
- Note that on Android you may need to scroll down to see this option as it’s below Delete
What does ITS do to help prevent phishing?
You are a critical step in helping to protect our shared computing resources. Security is best deployed in layers, so if one layer is breached, others can help protect those critical resources. In addition to the great work we do as a community by reporting and ignoring the requests in phishing emails, ITS has deployed tools and techniques to aid in your ability to detect a phishing message, and also prevent these messages from reaching your inbox. In February 2022, approximately 20% of all email sent to members of the Clark community were automatically kept from reaching your inbox. That’s almost 700,000 messages we didn’t have to delete! Some of these techniques are:
- We partner with organizations like Microsoft, Palo Alto Networks, and REN-ISAC to help us identify attributes of messages that we know are malicious, and we send those messages right to your Junk Email folder. With Microsoft as our email provider we are part of a large global community, potentially learning about malicious content after it impacts other users, and before it impacts Clark.
- If a message has a known malicious attachment, that attachment is replaced with a notice that an attachment was removed from the message before it is delivered to your Inbox.
- When you click on a link in most email, in real-time the link is scanned to see if it is sending you to a known malicious website. If it is, then you are redirected to a warning page notifying you the link was malicious.
- Faculty and staff may notice [EXT] appended to the subject of an email that originates from outside of Clark’s email system. If you see a message that looks like it may have come from a member of the Clark community, but it has the [EXT] tag in the subject, be suspicious, and maybe reach out to them in a new email (not a reply to that potentially fraudulent email) sent to their Clark account.
- Clark uses technology like SPF and DKIM to help identify legitimate messages that do originate from outside our email system.